The 7 Biggest Threats to Decentralized Finance [Part 2]

Into blockchain technology since 2013, Vladislav Dramaliev is one of the founders of the Bulgarian crypto community. Head of Communications in the æternity blockchain project for three years, Vlad is currently focused on his crypto donation platform BitHope.org, the monthly Sofia Crypto Meetup event, and Decentralized Finance applications.
The decentralized finance (or DeFi) blockchain movement is on a quest to reimagine finance on public blockchain infrastructure, empowering users with more transparent, trustless, efficient, and user-friendly services.
The projects in the nascent DeFi ecosystem are building a parallel global financial system where users are identified primarily by their crypto wallet keys and can make use of leveraged trading, money markets, decentralized exchanges, peer-to-peer lending and borrowing, insurance, portfolio management, and various other traditional and brand new value propositions. It is a brave new world founded on cutting-edge technology and research. It is also a vision that will take years to fulfill with dangers at every step on the way.
In this two-part series, we explore seven of the most noteworthy challenges the DeFi industry is currently facing and offer mitigation strategies for each. In the first part we discussed:
- Ethereum non-scalibility
- The effects of a potential Maker and DAI stablecoin failure
- Smart contract bugs and hacks
+++Access Part 1 of Biggest Threats To Decentralized Finance here.+++
This article will focus on the final set of threats, including:
- Oracle manipulation
- Admin keys
- Composability
- Permissioned stablecoins
Let’s jump in.
1. Oracle Manipulation
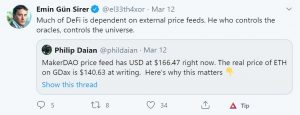
How do Maker’s smart contracts know the current price of ETH used to determine if the collateralization ratio is kept? They use data providers called “oracles.”
Oracles are essential for the DeFi ecosystem since they supply market data that settles financial [smart] contracts.
The most common type of oracle information that DeFi applications use is price data. Mostly, oracles reply to queries like “What is the current price of token X”?
Knowing the prices of assets enables their trustless exchange, service applications like Synthetix, Uniswap, Kyber, and Bancor provide. Oracle data is also used to determine the level of collateralization and capitalization in lending DeFi protocols such as Aave, Dharma, and Compound. Finally, the price feeds that oracles provide trigger automatic rebalancing in portfolio management protocols like TokenSets.
What if there is a bug or someone manipulates the information provided by the oracle?
Incorrect price data was behind the abnormal behavior of the Synthetix protocol on June 24, 2019. Due to an oracle malfunction, the Korean Won’s purchasing power skyrocketed, allowing KRW holders to purchase ETH at a significant discount.
Similarly, on February 15, 2020, a profoundly technical user managed to manipulate the price of wETH, decreasing it and profiting 330k USD. That was possible since the used DeFi protocol – bZx – relied on a single oracle for the value of wETH – the decentralized exchange Uniswap.
Three days later, on February 18, 2020, a hacker managed to perform another similar attack on bZx, which manipulated the price of sUSD on the Kyber exchange, doubling it from 1 USD to 2 USD. That allowed them to exchange sUSD for ETH, earning 2378 ETH in profit (valued at 635k USD at the time). That was again possible due to Kyber’s reliance on a single oracle.
On March 12, 2020, DAI’s USD/ETH price oracle stopped providing data to MakerDAO’s loan management system, leading to a delayed and, subsequently, sharp increase in loan liquidations.
Mitigation
Instead of depending on a single source of information, especially one that is easily manipulated due to limited liquidity (ex. Uniswap), DeFi projects must employ a more reliable oracle setup. Projects usually design those themselves or implement a third-party solution.
After the two oracle manipulations, bZx announced that they are incorporating Chainlink’s oracle services. Implementing Chainlink’s decentralized oracle solution, each of bZx’s critical price feeds is now secured by independent nodes, which collectively source data from over 7 independent data aggregators. Aave, Synthetix, Nexus Mutual, and TokenSets all rely on data feeds coming from Chainlink.
The darker side of this success story is that Chainlink’s oracle services are becoming a systemic risk to DeFi and any other dАpps that use them (Chainlink serves non-Ethereum platforms as well). Put simply, Chainlink is a single point of failure in DeFi (and blockchain).
Unwilling to expose their users to third-party risk, Compound have devised their own oracle solution. It calculates the median price of BAT, REP, ZRX, and WBTC as delivered by the APIs of the centralized (and liquid) Coinbase Pro, Bittrex, Poloniex, and Binance exchanges and posts it on-chain. Price updates happen when there is a 1% difference between the last reported price and the market price for each of these assets. Similarly, MakerDAO has developed its price feed solution.
A more recent approach addressing the oracle dilemma was suggested by the UMA protocol and is currently applied in Balancer’s Beta. It relies on arbitrageurs, economically self-interested third parties, to buy or sell tokens pushing the price closer to market reality. It remains to be seen how well that solution performs in the wild.
For a full overview of how some of the most popular DeFi projects address oracle manipulations, visit this curated list in GitHub prepared by Linda Xie.
2. Admin Keys / Access to Users’ Tokens
Another popular designation for Decentralized Finance is “non-custodial finance.” The title implies a differentiation with traditional finance services (like centralized exchanges and banks) where users’ funds are controlled and secured by a company or institution. Non-custody refers to the idea that instead of humans, users’ tokens are managed by inanimate pieces of programming code known as smart contracts.
That claim has important legal implications. Since custodial services are heavily regulated, presenting a project as non-custodial helps the team behind it dodge burdensome legislation (and save tons of cash).
On the other hand, the message is entirely in line with the philosophy behind blockchains. Namely, that trust must be transferred from the hands of the few to independent, cryptographically secure silos that enable users to have uninterrupted and unconditional access to their funds.
In reality, “non-custody” is more of an end goal in DeFi than a current state.
The main reason for that is the existence of admin keys. They allow developers behind a DeFi project to control the smart contracts that manage user funds. There are at least two good reasons why this is necessary.
First, DeFi dapps are software. Since no code is created infallible or flexible enough to accommodate all customer needs on the launch, finance apps on a blockchain require updates. How do you update a piece of code that you can not access? Simple, you don’t (yes, ok, you can hack it, not the point).
Second, what if a force majeure situation manifests itself and exposes users’ funds? Accessing smart contracts’ main levers (including the on/off button) could be the difference between a bruised public image and jail time. Here is an example.
Тhe existence of an admin key does not automatically presuppose access to users’ tokens. However, that is the case in eleven out of the fourteen notable projects reviewed by DeFi Watch by Chris Blec. Once it is clear that the team behind a DeFi project has access to the users’ crypto, it is crucial to consider the type of access. There are several different flavors there as well.
Some projects feature a multisig setup, requiring a certain minimum number of signatures (approvals) to institute a change in a smart contract. The most common implementation types are the 2-of-3 and 3-of-5 ones. The main issue here is that, possibly due to security considerations, there is no transparency on who owns these keys in all DeFi Watch-reviewed projects but one – Nexus Mutual. It is entirely possible that a single individual has access to all of them, turning the security setup into a marketing stunt.
Apart from multikey access, timelocks constitute a vital protection mechanism. They enable users and developers to act in response to a code change before it is implemented. For example, in the case of Dharma, a smart contract code change is enforced seven days after it is merged with the main codebase. This gives users one week to decide whether they want to keep their funds in the protocol or move them. Timelocks could be particularly useful in cases where a malicious actor institutes the code change. In 2016, the 27-day timelock was what prevented the DAO hacker from spending three million stolen ether.
Despite the proven usefulness of timelocks, DeFi projects like Nuo and PoolTogether do not make use of them.
Mitigation
The most direct way to address the admin key controversy is not to have an admin key. Since that may not be practicable in an industry where the speed of innovation is measured in days, the next best approach would be to be transparent about the process used to modify a DeFi protocol.
The most community-acceptable best practice currently is to introduce a governance mechanism with a Decentralized Autonomous Organization (DAO). Maker has already implemented this approach, while Compound and Synthetix are moving in that direction. Using the DAO, users who own a governance-token (ex. MKR in Maker) can vote for or against code changes that impact the value proposition of the protocol. The hope is that more and more DeFi projects will be moving in that direction.
3. Composability / “Money Legos”
Composability is one of the most marketed features of decentralized finance protocols. It relates to their ability to seamlessly integrate, enabling faster growth, the sophistication of services, and even entirely new financial products. Here is a relevant quote from The Defiant:
“[DeFi] Protocols are built with open-sourced code on top of public and global networks, which means applications can integrate and work together, stacked and snapped into place in the way users find most useful.”
All disruptive technologies are controversial, however, and while the more audacious users focus on what is gained, the more conservative tend to consider the risks. The danger of composability is the creation of fundamental dependencies between DeFi protocols that could grow into systemic risks.
On the positive side, code interconnectedness allows the PoolTogether smart contract to automatically transfer users’ funds into Compound, where they earn interest (the lottery prize). Furthermore, the 1inch DEX aggregator is integrated with the most liquid decentralized exchanges and allows users to make the most profitable exchange for any available token pair. Thanks to composability, the exchange is executed directly from the 1inch interface.
The more controversial side of interconnectedness in DeFi was recently exemplified by the bZx hack mentioned in Part 1. The attack involved a brand new DeFi service called a “flash loan.” Here is what a flash loan is, according to CryptoBriefing:
“Flash loans are smart contracts that allow users to take out uncollateralized crypto loans and then pay them back within the same Ethereum transaction. It offers borrowers access to massive amounts of liquidity.”
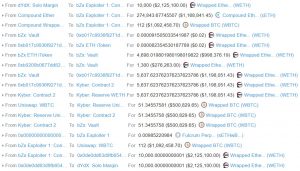
Using a flash loan, an attacker executed a composability-enabled exploit involving dYdX, Compound, bZx, Kyber, and Uniswap, siphoning $330,000 worth of tokens from bZx. Here is what the hacker’s transaction looked like:
Mitigation
In reality, DeFi is not that composable yet. According to Zerion co-founder Evgeny Yurtaev:
“Instead of legos, DeFi is more like a puzzle, where each developer brings their own pieces to the table, and though they look alike and are meant to build the same picture, these pieces don’t really fit together.”
Current examples of composability are the result of a concerted effort on the part of developers to make protocols connect. “Forced-compatibility” is even more dangerous since it increases the complexity and widens the attack surface. What is the solution?
Apart from the standardization of DeFi interconnectedness that helps developers achieve elegant composability, an effective way to mitigate risks would be through frequent code audits.
As discussed in Part 1, smart contract security is fundamentally important to the generation of trust in the DeFi space. There are already several companies that offer such services to DeFi teams, including Consensus Diligence, Zeppelin, Sigma Prime, and iosiro. Establishing and applying security best practices in the space brings substance to the composability-focused marketing claims.
In an interconnected universe of DeFi protocols, taking care of one’s own project’s security demonstrates solidarity towards your peers. Be wary of projects that exhibit a lack of transparency of code audits.
4. Decentralized Finance, Centralized Stablecoins
Perhaps one of the most notable points of systemic failure in the crypto space (apart from centralized exchanges) is stablecoins. Token affectionados have a love/hate relationship with them. On the one hand, they provide a convenient on-ramp for newbies and a vestige of price stability for traders, on the other they bring massive amounts of centralization and a hint of “fractional reserve banking,” much dreaded in the public blockchain space.
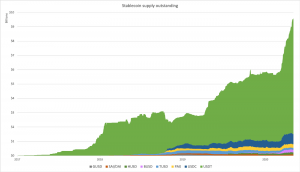
It is evident from the chart above that the supply of stablecoins in Ethereum, and especially Tether (USDT), has skyrocketed. Furthermore, most of the value transacted in Ethereum is now coming from USDT, USDC, BUSD, and DAI.
Having Maker as the project that launched the DeFi movement says a lot about stablecoins’ importance in the DeFi ecosystem. Despite its shortcomings, a programmatic token that is softly pegged to the US dollar and collateralized with ETH is a big leap for blockchain finance. After the Black Thursday (March 14, 2020) market crash and DAI’s undercapitalization, however, the Maker community decided to add the Coinbase- and Circle-backed USDC stablecoin to the mix of collateral types.
Indeed, the importance of USDC has gradually grown in the DeFi space. Currently, Compound’s smart contracts store 28m USDC, Maker utilizes 13m USDC, Aave’s holdings amount to 6.3m USDC, and dYdX manages 7.3m USDC. It is safe to assume that about 10% of all available USDC is stored in DeFi. That could be a problem.
Despite being more transparent than the notorious USDT, USDC is still fully controlled by a centralized entity – Coinbase. Any USDC tokens can at any time be deemed worthless if someone at Coinbase has a bad day. Ok, that’s gross a gross simplification. It is probably not that easy, but it is definitely not impossible. Permissioned stablecoins are sort of a Trojan’s Horse in DeFi. Imagine Maker’s DAI becoming undercollateralized by 13m USDC because a US regulator decided that Maker is in breach of some securities law. Solutions?
Mitigation
Unfortunately, there is no clear resolution to this issue. Stablecoins provide a critical function in both the crypto world and DeFi, and their importance will most likely continue to grow. Even DAI, the best alternative in existence, is now partly at the mercy of a US company.
Perhaps, DeFi teams and communities should refuse to add fiat-backed stablecoins. Another solution could be to distribute the centralization risk by incorporating different types of collateral into DAI.
Centrifuge, for example, is trying to bring non-fungible invoices-backed tokens to back DAI minting. The process of tokenizing real-world assets and using them as collateral to back trustless stablecoins is just starting. That just may be the way out of the centralized stablecoin deadlock.
_________
* Disclaimer: The author of this article is neither an investment advisor nor broker-dealer. The information presented is provided for informative purposes only and is not to be treated as a recommendation to make any specific investment.
__________
If you found this content valuable, follow Vlad Dramaliev on Twitter and follow his column on Trending Topics.