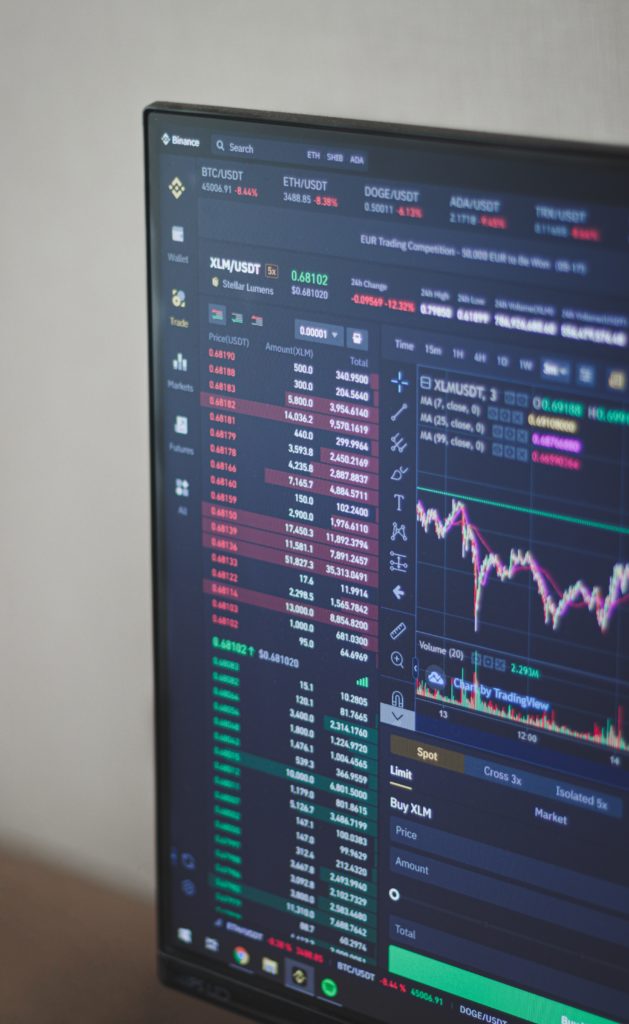
The biggest crypto trends of 2024 | Part 1

Ed Prinz is co-founder and CEO of Loob.io, a digital marketplace for blockchain assets, and chairman of DLT Austria, a non-profit organization promoting blockchain technology. This is the first part of his three-part series on “Crypto Trends 2024”.
A look ahead to 2024 in the fascinating world of blockchain technology reveals a landscape of digital innovation that is constantly in flux. Often it is the humble beginnings that lead to the most significant changes. Just think of the introduction of the iPhone in 2007, which sparked a revolution in the smartphone industry despite initially less-than-ideal technological conditions.
Today, we are witnessing similarly exciting developments in the world of crypto assets that are exceeding our expectations and opening up new horizons. This 2024 outlook offers insight into the fascinating advances and trends that could shape the coming years.
The key concepts of crypto & blockchain
We will first look at the key concepts of cryptography, including zero-knowledge, multi-party computation, and post-quantum crypto, which form the foundation for safer and more efficient blockchain technology.
- The vision of a decentralized energy future in which blockchain technologies play a central role is an important aspect. We will explore how blockchain can fundamentally change the way energy is produced, distributed, and used.
- User experience in the crypto world is also a focus of our outlook. New approaches to simplicity and security will significantly improve interaction with crypto assets and decentralized applications.
- In gaming, we will examine the evolution from “earn to play” to “play and earn,” with blockchain technologies putting players at the forefront like never before.
- The exciting merger of artificial intelligence and crypto assets will usher in a new era of decentralized innovation, where intelligent agents and algorithms play a crucial role in blockchain networks.
- Another highlight is the simplification of the formal verification of smart contracts, which leads to more robust and secure applications. This development promises increased reliability and trustworthiness in smart contract-based projects.
- Lastly, we will take a look at the revolution in calculation verification brought about by ZK-SNARKs, making calculation verification more efficient and secure. This technology makes it possible to verify complex calculations without revealing sensitive data, thereby strengthening privacy and security in the blockchain world.
This 2024 outlook for the world of crypto assets promises exciting developments and innovations that could fundamentally change the way we do business, communicate, and interact. It is a time when technological advancements will impact not only the blockchain industry but also many other areas of our daily lives.
Zero Knowledge, Multi-Party Computation, and Post-Quantum Crypto
The world of cryptography is constantly evolving, and a few key concepts are currently in focus: zero-knowledge proofs, multi-party computation, and post-quantum cryptography. These technologies are fundamental and have far-reaching implications for blockchain scalability, application security, and more. However, there are still many challenges and trade-offs that need to be addressed.
An important topic is zero-knowledge proofs (zk-proofs). This is about how well someone can prove something, how short that proof is, and whether you need a trustworthy body to do it. It will be exciting to see whether there will be new methods for ZK proofs that better balance these points. What is particularly interesting is whether you always need a trustworthy body to check short evidence. This would show how important it is that these bodies are clear and trustworthy.
Another important area concerns constructions for threshold ECDSA signatures (Elliptic Curve Digital Signature Algorithm). Achieving thresholds eliminates the need to trust a single signer, which is critical for multi-party computations involving private data and applications on Web3. Of particular interest are Threshold ECDSA signatures that minimize the total number of rounds, including pre-signature rounds where the message is not yet known.
In the digital world, identity verification is more complex than in face-to-face conversations, where we often confirm a person’s identity through their face, voice, or introduction by someone we trust. On the Internet, for example, when a user connects to their banking provider, they need not only security for information being transferred but also the assurance that they are sending it to their bank and not to a malicious website that impersonates their provider. This assurance is provided by the Transport Layer Security (TLS) protocol, which uses digitally signed identity credentials (certificates). Digital signature techniques also play a central role in DNSSEC, an extension of the Domain Name System (DNS) that protects applications from forged or manipulated DNS data, such as DNS cache poisoning.
A digital signature is evidence of authorship of a digitally transmitted document, conversation, or message. Similar to traditional signatures, it can be publicly verified by anyone who knows it was created by a specific person. The digital signature process consists of three main components: a key generation algorithm that creates a key pair from a public verification key and a private signing key; a signature algorithm that uses the private signing key to create a signature for a message; and a verification algorithm that uses the public verification key, the signature, and the message to determine whether the signature is valid.
In the Transport Layer Security (TLS) protocol, authentication must occur when establishing a connection or conversation, as data sent thereafter is automatically authenticated unless this is explicitly disabled. Therefore, the transition to post-quantum secure signatures is not as urgent as with post-quantum key exchange methods, as there are currently no sufficiently powerful quantum computers available to eavesdrop on connections and forge signatures. However, this will change in the future and the transition will become necessary.
There are several candidates for authentication schemes (including digital signatures) that are secure against quantum attacks. Some use cryptographic hash functions, others are based on grid problems, and others use techniques from the field of multi-party computation. It is also possible to use key encapsulation mechanisms (KEMs) in cryptographic protocols for authentication.
The construction of a specific post-quantum secure signature method, such as CRYSTALS-Dilithium, is a finalist in the NIST process to standardize post-quantum cryptography and illustrates a common approach to developing digital signature methods. Dilithium is a technology that uses polynomials and mathematical rings. Imagine you have a special set of equations that allows you to add and multiply numbers. Dilithium creates a special kind of matrix, a table that contains these equations and secret series of numbers. The public key, which everyone can see, is created from this matrix and a special calculation. Quantum computers have a hard time finding the secret numbers in this calculation, which makes them secure.
Dilithium is about verifying identities and signatures. The one who wants to prove his identity creates a secret value and a kind of digital promise. The examiner issues a challenge. The person providing evidence responds with a possible digital signature and checks whether it is secure. The examiner then looks to see whether this signature matches what he expects. The technique that transforms the whole thing into a type of signature that works without direct exchange is called the Fiat Shamir transformation. This also makes the process safe against quantum computers.
In summary, as new post-quantum secure signatures are close to standardization, it would be worthwhile to investigate which of these signatures might be suitable for aggregation or thresholding. This could further improve security and efficiency in the post-quantum era.
Decentralized energy systems and blockchains – A realistic vision for the future?
In this paragraph, we explore the application of the decentralization philosophy in the energy sector. Currently, most power grids are outdated and centralized, creating challenges such as high costs and uneven incentives. However, there are exciting opportunities to address these issues. We discuss the development of microgrids, storage, and transmission networks in which tokens play a crucial role.
Another focus is on emerging markets for renewable energy certificates and carbon credits based on blockchain technology. These developments are groundbreaking for a decentralized energy supply in which blockchains take over the coordination. We’re excited to see how developers in this space continue to push the boundaries of what’s possible and thereby redefine the future of energy supply.
The electrical grid is a complex and extensive network, with parts dating back over a century. Energy is a crucial lever for reducing environmental impact. Today’s world is characterized by natural disasters and the environmental effects of climate change. These problems are closely related to the global energy system. The decentralization of the energy system is not only in line with Web3 ethics but is also crucial for environmental protection.
A look at the fundamental principles makes the possibility of decentralizing the energy system clear. The earth’s resources for renewable energy are enormous compared to our needs. The use of solar energy has great potential because sunlight is available everywhere in the world. Electrifying energy-dependent applications allows us to reduce environmentally harmful centralized fossil fuel supply chains. Similar to the vision of IPFS and Filecoin, where large centralized data centers are replaced by a distributed network of miners and nodes, we can significantly increase the sustainability of our society by producing energy closer to the point of consumption.
Today’s power grid is designed to transport electricity from a small number of large generating facilities to a large number of consumers. Historically, this was cost-effective and easier to control. However, decentralization requires redesigning control systems to enable coordination without centralization. This is a complex challenge that can only be implemented gradually. Development is required to address the complexity of the power system by breaking down basic tasks into deep modules with simple interfaces that enable upgrades and minimize overall complexity.
Distributed energy generation offers numerous advantages, including environmental friendliness through renewable energy sources such as PV, wind power, and more, low environmental impact compared to fossil fuels, and short transport routes for electricity and heat. It also enables energy independence from central providers and reduces price fluctuations. Decentralized energy systems increase the resilience of communities to natural disasters and create jobs. Although initial investments are required, they result in significant long-term cost savings from self-generated energy.
In addition to its advantages, decentralized energy generation also has some disadvantages. A significant hurdle can be the initial investment in the required equipment, as operators must first provide financial resources. In addition, decentralized energy systems such as photovoltaics and wind power are weather-dependent, which can lead to fluctuations in energy production compared to biomass and biogas. A solution to this could be the use of various decentralized systems.
Decentralized energy production will become increasingly important in the future as a decisive factor in the global energy transition and in the fight against climate change. This trend is driven by technological advances in renewable energy and energy storage, the digitalization of energy infrastructure, the use of distributed ledger technologies, the formation of energy communities, and policy measures. It is expected that decentralized energy systems will play an increasingly important role in energy supply.
User experience revolution in the crypto
In the world of crypto assets, we are currently witnessing a significant evolution in user experience (UX) that is groundbreaking for the future. Traditionally, UX in the Web3 space has been challenging, especially for new users. With the need to self-manage private keys, connect wallets to decentralized applications (dApps), and manage signed transactions across different network points, the barrier to entry was often high. However, a transformation that could fundamentally improve the user experience is underway.
A key innovation in this area is passkeys. They have the potential to revolutionize the way we log into apps and websites. Unlike traditional passwords, which are often subject to security risks, passkeys are cryptographically generated and work seamlessly across a user’s devices. This approach not only simplifies the login process but also increases security.
Another advance is the concept of Smart Accounts. Because they are programmable, they are easier to manage. These accounts automate certain functions and offer more intuitive control options, making interactions with crypto services much easier.
The integration of wallets directly into applications, known as embedded wallets, is also a significant innovation. They make it easier for users to get started with crypto services because the necessary tools are already integrated into the application environment.
Multi-Party Computation (MPC) technology offers a further improvement. It allows third parties to assist in signing transactions without having to hold the user’s keys. This offers a safer and more user-friendly way to manage crypto transactions.
Finally, advanced RPC (Remote Procedure Call) endpoints help simplify the user experience. These endpoints are designed to understand user intent and automatically fill gaps in the transaction process. They make the user experience more intuitive and reduce the likelihood of errors.
All of these developments not only help make Web3 accessible to a wider audience but also provide a better and safer UX than what is currently available in Web2. The focus is on reducing complexity, improving security, and creating a more user-friendly interaction with Web3 applications. This transformation could be a significant step towards the widespread acceptance and use of crypto assets and blockchain technologies.
From “Play 2 Earn“ to „Play & Earn“: The volution of Gaming?
The gaming industry is one of the world’s most popular sectors with a huge player base across various platforms. In recent years, game developers have shown increased interest in incorporating blockchain technology to create innovative games.
“Play to Earn” (P2E) became popular in the 2020s, allowing players to earn in-game tokens as rewards by completing quests, winning battles, or creating assets and experiences in games. These tokens could then be exchanged for fiat currency on special markets. Although P2E was initially seen as a groundbreaking model for blockchain and metaverse game monetization, popular P2E games like Axie Infinity have recently seen a decline in user engagement and native token prices have fallen. This has brought solutions such as “Play and Earn” (P&E) into focus.
Play and Earn (P&E) emphasizes improving the gaming experience while still providing rewards. In contrast to P2E, the focus of P&E is not only on financial incentives but also on the enjoyment of playing the game itself. P&E games are designed to be entertaining in the long term and to motivate players to actively participate.
There are several differences between P2E and P&E. P&E games prioritize the gaming experience, while P2E games often aim for financial rewards. In terms of market dominance, P2E games are currently more common, but P&E is also gaining traction and offering a better gaming experience. Another important aspect is the distribution of value between players and developers. P&E enables a more balanced distribution of value, where players are involved long-term and can support developers.
In terms of features, both P2E and P&E offer unique advantages. P2E offers smart contracts and decentralized control over assets, while P&E offers digital assets as rewards and grants full ownership rights.
Despite the initial popularity of P2E (Play to Earn), it ultimately met its demise when the bear market set in and depressed token prices. The main problem that users had with this genre was the unsustainability of its economy.
In any economy, a healthy balance of supply and demand is crucial to keeping it functional. P2E games were designed to rely on supply and demand, but their economy was entirely dependent on it.
Most P2E games relied heavily on continually attracting new users to support the economy. While P2E games were able to thrive in this environment, they could only survive in it for so long. Ultimately, when a game failed to attract enough new players or when sales of in-game items dropped significantly, those games collapsed under the cost of their own operations and became victims of their own success. Many popular P2E games had already failed before the bear market began.
If the main incentive for players is to make money, users often lose interest once the opportunity to make profits disappears. This results in a game made up mostly of investors and speculators, with real players being rare.
The evolution from “Play to Earn” to “Play and Earn” reflects a shift in the gaming industry. Originally, players could earn real money in “Play to Earn” games. This approach is now expanding to prioritize the fun of gaming while allowing players to share in the value generated. This shift highlights the need to make games both entertaining and economically rewarding, and to find a balance between fun and monetary reward.
AI and Blockchain: A New Era of Decentralized Innovation?
The fusion of artificial intelligence (AI) and blockchain represents a balance between centralized AI systems and decentralized approaches. To date, large technology companies have dominated the development of AI, but crypto assets opened new avenues for broader participation and rewards in global markets . This could reduce the cost of AI and increase its accessibility. At the same time, crypto assets technology enables tracking the origin of digital content and contributes to the decentralization and democratic control of AI, increasing consumer security.
In the world of Web3 games and future video game development, it is becoming clear that AI agents in games must provide certain guarantees. These guarantees include the use of specific models and ensuring their unaltered execution. When AI systems play a central role in game development, it is crucial to ensure that they act in a credible and neutral manner. Players want to be assured that the game world is based on solid foundations. This is where blockchain technology can contribute by providing such guarantees, including the ability to adequately detect, diagnose and address AI problems.
In this context, it becomes clear that “AI alignment” is essentially an incentive design problem, similar to when dealing with human actors. This reflects the core of what the world of crypto assets is all about.
However, software vulnerabilities can have serious consequences, including crashes, data loss, and security breaches that affect the quality of software applications. Traditional approaches to troubleshooting, such as automated testing and static analysis tools, face challenges, particularly when it comes to false positives. An innovative approach based on Large Language Models (LLMs) tailored specifically for cybersecurity could revolutionize the detection of software vulnerabilities. LLMs could achieve an impressive accuracy rate of over 90% in identifying vulnerabilities and have a significant impact on cybersecurity.
Another focus is on an innovative solution that combines LLMs with formal verification strategies to verify and automatically remediate software vulnerabilities. This approach uses constrained model checking to identify vulnerabilities and derive counterexamples. These counterexamples are then passed to the LLM system, which uses a specialized prompting language to debug and repair the code. The results of this method could be promising as it could successfully repair vulnerable code, including buffer overflows and pointer dereference errors.
Overall, the combination of AI and blockchain could help improve the security, transparency and efficiency of AI systems. This could lead to broader application of AI across different industries while preserving users’ privacy and maintaining control over their data.
Simplified Formal Verification for Smart Contracts – Highest security standards in the world of blockchain?
In the world of software development and system design, formal methods play a crucial role. These mathematical techniques and tools are designed to improve the quality, security and reliability of software and systems. They rely on formal logic and mathematics to bring precision and clarity to the development process.
A critical aspect of formal methods is the ability to produce precise and unambiguous specifications. This prevents misunderstandings and misinterpretations during the development process.
Verification of software or systems is a critical step to ensure their correctness. Formal methods enable mathematical verifications that allow developers to prove the correctness of a system. This is particularly important in safety-critical applications where errors can have devastating consequences.
The ability to model systems abstractly is another feature of formal methods. This simplifies the analysis of complex problems by removing irrelevant details.
Formal methods use mathematical proofs to demonstrate the correctness of systems, resulting in higher trust and quality. Formal methods find application in various areas, particularly in safety-critical industries such as aerospace, medicine, automotive and finance. However, they are also widely used in general software development.
Despite their advantages, formal methods are not without challenges. They often require deep mathematical knowledge and can slow down the development process. Nevertheless, they are an essential part of modern technology development.
In a world where software and systems play an increasingly important role, formal methods will continue to contribute to the development of safer, more reliable and higher quality solutions. They are the mathematical basis for the software quality of tomorrow.
While formal verification methods are widely used in the world of software development, they often seem too complex and cumbersome for most developers outside of specialized areas such as safety-critical hardware. However, this changes in the context of smart contracts, where the requirements for security and reliability are particularly high.
Smart contract developers face the challenge of creating systems that manage billions of dollars, and errors in these systems can have devastating financial consequences. Unlike traditional software, smart contracts typically cannot be updated through patches because they run on blockchain platforms.
In recent years, a new wave of tools has emerged specifically for the formal verification of smart contracts. These tools provide a better developer experience compared to traditional formal verification systems. The reason for this lies in the architectural simplicity of smart contracts: they are characterized by atomic and deterministic execution, the absence of concurrency or exceptions, low memory consumption and minimal loops.
Another significant advance is the performance of these tools, which benefit from recent breakthroughs in the performance of SMT (Satisfiability Modulo Theories) solvers. SMT solvers are complex algorithms used to identify errors in software and hardware logic or to confirm the absence of errors.
The increasing use of tools inspired by formal methods has the potential to significantly increase the robustness of smart contract protocols and make them less vulnerable to costly security breaches.
ZK-SNARKs: Is this finally the revolution in the verification of calculations?
Verification of calculations has played a crucial role in the world of technology. There are different approaches to ensure the trustworthiness of calculations. One of these approaches is to rerun the computation on a machine that is considered trustworthy. This is a reliable method but comes with its own costs and scalability limits.
An alternative strategy is to perform the computation on specialized machines known as Trusted Execution Environments (TEE). While this can work around some problems, it is not always practical.
Another option is to perform the calculation on a neutral infrastructure such as a blockchain. This approach shows promising possibilities, but also faces its own challenges.
Recently, an exciting development has emerged that has the potential to fundamentally change the way calculations are verified: ZK-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge). ZK-SNARKs enable the creation of a “cryptographic proof” of a computation by an untrusted “prover.” This is notable because it is virtually impossible to forge such a receipt.
However, in the past, creating such a document involved significant additional effort, approximately ten times the original calculation. This was a significant disadvantage. However, thanks to recent advances, we are moving towards an additional effort of only one-millionth of the original calculation.
What does that mean? It means that ZK-SNARKs become practical in situations where the original computation provider can bear this overhead, while customers may not have the ability to re-run or store the original data.
The potential use cases for ZK-SNARKs are diverse. For example, edge devices in the Internet of Things could verify upgrades, media editing software could embed authenticity and transformation data, and even redesigned memes could express appreciation for the original sources.
But that is not all. ZK-SNARKs could also enable authentic LLM inferences. For example, self-verifying IRS forms that cannot be falsified or bank audits that are secure against tampering.
The introduction of ZK-SNARKs promises to revolutionize the verification of calculations in the world of technology. They provide the ability to verify calculations in a new way and open up a world of use cases that can benefit consumers and businesses alike. It will be exciting to see how this technology develops and what impact it will have on the way we verify calculations in the future.
Conclusion and Closing Remarks 2024
The year 2024 will be marked by significant developments in cryptography. Key concepts such as zero-knowledge proofs, multi-party computation, and post-quantum cryptography are crucial. The further development of ZK-SNARKs and Threshold ECDSA signatures improves efficiency and security. Post-quantum signatures offer new security perspectives. A decentralized role for blockchains is emerging in the energy sector, with developments such as microgrids and blockchain-based energy certificates. The crypto assets world is experiencing a significant improvement in user experience through new technologies such as passkeys and MPC.
In the gaming sector, the model is changing from “play to earn” to “play and earn”, and the combination of AI and blockchain promotes democratic control. The security of Web3 games and the integrity of AI agents is strengthened by cryptography. The formal verification of smart contracts is simplified by new tools, and ZK-SNARKs open up new application possibilities. The future holds exciting innovations in cryptography, blockchain and AI that will impact diverse industries. The choice between modular and monolithic architecture is critical to the future of networking technologies.
2024 promises fundamental changes in business, communication and interaction, and could exceed our expectations in blockchain technology.
In Part 2 we will look at the two leading crypto assets, Bitcoin and Ethereum. Don’t miss this detailed sequel.
Disclaimer: This is my personal opinion and not financial advice. For this reason, I cannot guarantee the accuracy of the information in this article. If you are unsure, you should contact a qualified advisor you trust. No guarantees or promises regarding winnings are made in this article. All statements in this and other articles represent my personal opinion.